#1 Spyware Guide in 2022
Spyware threats have been ruthless in recent years. That’s why it’s crucial to learn as much as possible about spyware and related threats to keep your computer, smartphone, and other devices safe. This article covers everything you need to know about spyware. You’ll learn what it is, if you’re at risk of being exposed to spyware, how to get rid of it, and a lot more.
What is spyware?
Spyware is a term that describes different types of malicious software that can track your computer activities or steal sensitive data.
It can affect both consumers and businesses as long as their desktop or mobile devices have an internet connection. That data often includes credit card or bank account information, usernames and passwords, and more.
Spyware sends this personal data — without the owner’s permission — to hackers or criminal organizations who use it illegally for their gain. The benefit is often financial, but other uses, such as spying, are also common.
Corporations can also install spyware on their employees’ computers to keep an eye on their online activities. However, this is not technically illegal. Spyware refers to the usage of tracking software with the intent to steal users’ personal data.
Think of spyware as an enemy spy that gathers vital information — it can be hard to detect. Once it has infiltrated your device, you must be alert to the signs of malware infection to know that your device has been affected. The good news is that once you know the telltale signs of infection and have a reliable antivirus program, you’ll get rid of most spyware types from your device.
Spyware refers to the usage of tracking software with the intent to steal users’ personal data.
Statistics
We’ve compiled a few statistics to help you get an idea of how harmful spyware is. Our goal is not to scare you, but to inform you about the dangers of having weak security on your device or computer.
According to McAfee and the Center for Strategic and International Studies (CSIS), the cost of global cybercrime reached over 1 trillion dollars from 2018 to 2020 — that’s more than 1% of the global GDP!
Additionally, according to Verizon’s 2021 Data Breach Investigations Report, the median loss for data breach incidents was $21,659. Phishing attacks, which often include attachments with spyware, account for more than 80% of reported security incidents.
Avast has also investigated the impact of spyware on individuals — more specifically, those who use mobile devices. Based on a 2020 report from Avast, Android malware increased by 38% in the past year.
Moreover, adware, which can inject spyware on your device, accounts for 72% of Android mobile malware. Adware is software that hijacks a device to spam users with unwanted ads. Many of these ads can be highly damaging. The remaining 28% included banking Trojans, fake apps, lockers, and downloaders. We’re going to talk about these in detail below.
Android malware increased by 38% in the past year.
Also, according to Malwarebytes’ 2021 State of Malware Report, the number of spyware attacks on consumers increased by 24% from 2019 to 2020.
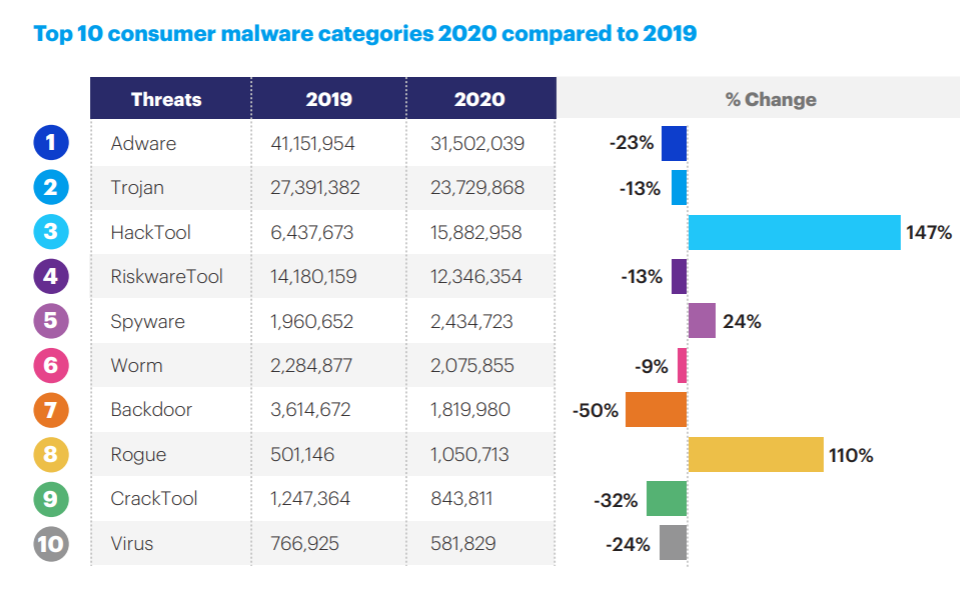
Source: Malwarebytes’ 2021 State of Malware Report
Who does spyware target?
Anyone who uses a computer or mobile device connected to the internet is at risk of becoming a victim of spyware. The Windows operating system is the most targeted OS, mainly due to its popularity, but also its vulnerabilities.
However, that doesn’t mean that Mac users are entirely risk-free. According to Malwarebytes’ State of Malware 2021 Report, malware targeting Macs grew faster than Windows in 2019, but, in 2020, detections decreased by 38%, though Mac detections for businesses increased 31%.
Android and iOS devices are also frequent targets of spyware, although the former is more targeted. On Android, HiddenAds — a form of aggressive adware — racked up 704,418 detections, an increase of nearly 149% from 2019 to 2020.
Furthermore, since most attackers seek financial information, those who use online banking are most at risk. In this respect, both individuals and companies are at risk. Businesses need to pay special attention to the security of their employees’ devices to avoid espionage and substantial losses.
Source: Malwarebytes’ 2021 State of Malware Report
Source: Malwarebytes’ 2021 State of Malware Report
How do you get spyware?
These software programs deceive you into installing them through social engineering tactics (scam emails or SMS) and other methods.
In a nutshell, here’s how spyware can enter your PC/device:
Opening email attachments from suspicious senders
Visiting malicious web pages or websites
Downloading software from dubious sources
Accepting pop-ups or prompts without reading them first
Using pirate websites to download games, music, or movies
Neglecting software updates that enable vulnerability exploits
What harm does spyware do?
After infiltrating your device through one of the methods described above, spyware then silently waits for you to access your computer. From here, it will then dig for information without you knowing. There are multiple ways that corrupt software gathers data.
For example, if the spyware is a keylogging virus, it will attempt to record your keystrokes when you use your keyboard to log in to your bank account. This information will then be sent back to the hacker. Other spyware may capture screenshots or take control of your microphone and camera.
Spyware can collect almost any type of data, including:
Usernames and passwords
PINs
Credit card information
Keyboard strokes
Phone numbers
Contact names
If you neglect the warning signs, your computer risks permanent damage due to frequent system crashes or overheating.
How to know if you have spyware on your device
Although it runs quietly in the background, you can detect spyware by following these signs:
System performance is degraded — spyware may increase disk usage, network traffic, and CPU load.
Your device crashes unexpectedly, runs out of hard drive space, or heats up dramatically for no reason.
There are new toolbars and different default search engines in your browser.
Your security program is disabled for no reason — some spyware even removes competing malicious software!
Some settings of legitimate programs installed on your computer are changed.
You receive popups in both online and offline modes.
You receive error messages when using apps that have never shown these messages before.
Keep an eye out for these warning signs; if you find spyware on your device, scan it immediately. Use a reputable antivirus program for a complete diagnostic.
Defend your system from spyware: download an antivirus program now!
Types of spyware
Because spyware is a catch-all term for various forms of malware designed to steal data, it goes under many different aliases as you’ll see below.
Trojan
A Trojan virus/horse is a type of malware that pretends to be legit software (hence, the analogy of the ancient Greek Trojan horse myth) to fool users into installing it. A standard method that cybercriminals use to deliver Trojans to victims is through social engineering — via phishing emails, for example.
A Trojan virus can be disguised as a software update, a mobile app, a Word doc, or other various types of files. Trojans are used by hackers to install other forms of malware, such as ransomware, viruses, keyloggers, and other forms of spyware. As such, a Trojan — or the spyware that it installs — can be used to steal sensitive data, including usernames and passwords, credit card information, and more.
An example of a spyware Trojan is the banking Trojan. This one is used to steal credentials from financial institutions. Its sinister modus operandi is to modify transaction content or insert additional transactions in a completely hidden fashion. One of the most prevalent cyber threats of 2019 was the banking Trojan, Emotet, which caused millions of dollars worth in damages to companies around the world.
Source: IBM X-Force Threat Intelligence Index 2021
Password stealers
Like banking Trojans, password stealers aim to gather user credentials for nefarious purposes. However, instead of intercepting entered data, password stealers go for usernames and passwords stored in browsers, cookies, and other files stored on local hard drives. This type of spyware targets game accounts, bank accounts, and other accounts that store sensitive information.
Password stealers are popular weapons in the cybercriminal’s arsenal. According to Kaspersky, the number of victims of stealers increased by 60% in 2019. There were fewer than 600,000 victims in the first half of 2018 and more than 940,000 during the same period in 2019.
Adware
Adware is a type of malware that displays intrusive ads on your computer or mobile devices. It can be seen either in your browser or as a desktop notification or popup. It secretly installs itself on your device, usually bundled with legitimate software, and can spy on your browsing activities and slow down your computer.
Some types of adware are not necessarily harmful, such as those that track your searches and collect data about you. This information is then used to deliver custom advertisements to you. Other forms display malicious banner ads (malvertising) that transmit malware onto your computer — even if you don’t click on it!
Adware can redirect you to malicious websites if you click on its infected ads. You may also notice that your default homepage is different and that your web searches redirect you to other websites.
Did you know? Half of the attacks on education sectors in 2020 were adware and spam, according to IBM.
Keyloggers
System monitors, also known as keyloggers, are among the oldest forms of malware that are still popular today. It’s a form of spyware that monitors your computer activity, including your keystrokes; it can also take screenshots of your display screen, browsing activity, emails, and more.
These programs are often used legitimately by companies to monitor their employees. Governments, intelligence agencies, and law enforcement agencies also use keylogging for surveillance purposes.
Naturally, hackers also employ keyloggers to steal information from victims and use it to their benefit. Bad guys deliver keyloggers to devices through malware packages which often come from suspicious websites, scam emails, and fraudulent links.
...keyloggers are among the oldest forms of spyware that are still popular today.
Tracking cookies
Cookies are small text files that websites create on your local drive to store web activities, such as user logins, online browsing, downloads, or searches. They can speed up your browsing experience and enhance targeted online ads making them more tailored to your needs.
However, since hackers can take control of tracking cookies for their benefit, these files can be considered a form of spyware. If they wanted to, experienced hackers could easily recreate your log-in sessions and steal your sensitive information.
For this reason, some antivirus software sees tracking cookies as spyware, and many users prefer to delete tracking cookies regularly to prevent hacking attempts.
Rootkits
Rootkits are some of the most dangerous types of malware. They can control your desktop or mobile device at a deep level, making them very difficult to detect. They can disable your security software and can even be used to log into your machine as an administrator.
Cybercriminals can benefit from rootkits in many different ways given that they often contain several tools. They can be used to steal your online banking information, record your keystrokes, and install other forms of malware on your devices as they can be used to disable your software security solutions.
Spyware on Mac
Macs don’t usually get malware thanks to their robust digital protection features. However, according to Malwarebytes, Mac malware has seen a major jump in recent years. It decreased in 2020, but the number of attacks is still high. This is likely because Macs experienced an increase in market shares, making Apple computers a more attractive target to cyber thieves.
Furthermore, the macOS integrated security system is not as good at detecting “soft” forms of malware like adware and PUPs (potentially unwanted programs) as it is at detecting malware like worms or viruses.
One single app deserves credit for the majority of adware on Mac in 2019 — NewTab. NewTab is an adware/spyware program designed to redirect web browser searches to earn illicit affiliate revenue for the adware creators. How can it infiltrate your Mac’s strong defense system? In a tricky way, of course — via apps that also install Safari extensions.
...Mac malware has seen a major jump in recent years.
Spyware on mobile devices
Mobile spyware can monitor and steal all kinds of data from your phone: SMS texts, call logs, emails, photos, browsing history, location, and lots more. Cybercriminals can even take control of your phone via commands they send through SMS or remote servers. Both consumers and organizations can be targets of spyware attacks on mobile devices.
Spyware can affect mobile devices in several ways:
Operating system vulnerabilities — attackers can exploit flaws in a phone’s OS (Android and iOS). This is why developers frequently release updates; it’s also why you should always keep your OS updated.
Password-free Wi-Fi — you run the risk of spyware attacks whenever you connect to a free Wi-Fi network, for example, when you’re at an airport or cafe. To reduce the chances of a potential attack, avoid free or unsecured Wi-Fi connections.
Malicious apps — these refer to apps that users install via links from text messages and other suspicious links. To avoid malicious apps, always use Google Play Store or Apple’s App Store when downloading apps.
Both consumers and organizations can be targets of spyware attacks on mobile devices.
iPhone spyware
Even though Android spyware is more prevalent, that doesn’t mean iOS is risk-free. iPhones don’t usually get many threats, but some mobile spyware has been known to affect these Apple devices, too. For example, a powerful surveillance app, which was an Android spy app at first, was able to penetrate the App Store’s defense systems and made its way into the phones of unsuspecting users.
The app disguised itself as a carrier assistance app and was able to steal data including contacts, audio recordings, photos, and clips from unsuspecting victims. The app could even be triggered to listen in on people’s conversations through remote commands.
Spyware prevention tips
With the right knowledge and a bit of vigilance, you’ll be able to keep spyware threats away from your digital devices. Here’s how:
Don’t use Internet Explorer. This traditional browser has always been a frequent target for cyber attacks. Microsoft has replaced it with Edge — a more secure and reliable browser.
Have an active firewall. A firewall is a security feature that monitors and manages incoming and outgoing network traffic. It blocks any unwanted sources that may be attempting to connect with your device.
Disconnect the camera and microphone when not using them. Spyware can control your audio and video recording hardware without your consent.
Pay close attention. Open only emails that were sent by someone you know. Avoid clicking on pop-up ads and don’t download files from suspicious sources.
Use an ad blocker. Sorry marketers, but the banner ads that users see on almost every site can potentially contain malware. So, get an ad blocker extension to enhance security and speed up your browsing
Use a reputable antivirus program. Besides being vigilant with what you click on and what programs you use, it’s crucial to use a respectable antivirus program, such as Norton or McAfee. Aside from spyware, antivirus programs have real-time protection against threats and can detect millions of types of malware.
Spyware removal tips
To clean spyware from your device, follow these steps.
First determine which kind of spyware you have. If you’re unsure, run a complete scan of your device using an antivirus solution such as Bitdefender or Kaspersky.
If you have adware, it may be tricky to remove. In this case, you may need to check and restore your browser start page, search engines, and extensions.
Tacking cookies — you can use a cleaning app or built-in browser tools to remove cookies.
Trojan and other spyware — let your antivirus program remove this type of spyware.
Steps to take after spyware cleanup
Once you’re sure that you’ve completely removed spyware from your computer, take these steps to protect your computer and data from future spyware attacks:
Change the passwords associated with all of your accounts. This includes email and banking passwords.
Use randomly generated passwords of 8-10 characters.
Enable two-factor authentication for all your sensitive accounts.
Check the transactions of your banking accounts and let your bank know of any suspicious activity.
Always update your antivirus software, programs, apps, and operating system. Be sure to also enable automatic updates where applicable.
FAQs about spyware
What are some examples of spyware?
Spyware can come in many shapes and sizes. Examples of spyware include banking Trojans, password stealers, adware, keyloggers, tracking cookies, and rootkits. Buy a reputable antivirus software, such as Bitdefender, to defend your device against these threats.
How do I check for spyware?
You can check for spyware by scanning your device using a reliable anti-spyware solution (Bitdefender being one of them). In addition to detection, these programs can also help you get rid of spyware. You can also verify if your browser’s default search engine and homepage have been changed.
How do you stop spyware?
Cybercriminals have multiple ways to trick you into installing spyware. As such, you need to remain vigilant at all times. Don’t click on suspicious links, don’t visit malicious websites, and don’t click on pop-ups. Update your antivirus software and operating system regularly. For best results, download a trusted anti-spyware software like Bitdefender now!
Why is spyware dangerous?
Spyware is used to gather personal information, like usernames and passwords, associated with your banking accounts, social media, email, etc. Big corporations are also at risk of losing millions of dollars should one of their employees fall victim to a phishing attack that results in spyware being downloaded onto their device. A highly capable antivirus program can keep your digital goods safe and secure.
Is spyware a virus?
Strictly speaking, spyware is not a virus. A virus is another type of malware that requires a host (like your computer) to cause damage. It spreads from one device to another, changing the way each computer operates. Spyware, on the other hand, sits silently on your device and records critical information, such as your banking credentials, and sends it to the cybercriminal responsible for it.
In any case, every computer or mobile user can benefit from full-fledged antivirus software to prevent spyware, viruses, or other malware.
Octav Fedor (Cybersecurity Editor)
Octav is a cybersecurity researcher and writer at AntivirusGuide. When he’s not publishing his honest opinions about security software online, he likes to learn about programming, watch astronomy documentaries, and participate in general knowledge competitions.