Ransomware is one of the most devastating forms of cybercrime. It’s not uncommon for attackers to successfully extort vast sums of money from their victims. Sometimes, they extort victims for millions of dollars, with some victims willing to pay up rather than ignore the threat of data loss or exposure.
Throughout this post, we’re going to take an in-depth look at 93 ransomware statistics for 2022, including:
The number of ransomware attacks that have taken place
The types of businesses targeted
Extortion rates (in terms of US dollars)
And much more
We’ve gathered data from the latest industry reports on cybersecurity. We also update our statistics regularly to offer you the freshest perspective on ransomware, including how you can protect yourself.
The prevalence of ransomware attacks
Here are the most important statistics regarding the growth of ransomware in 2021 and 2022.
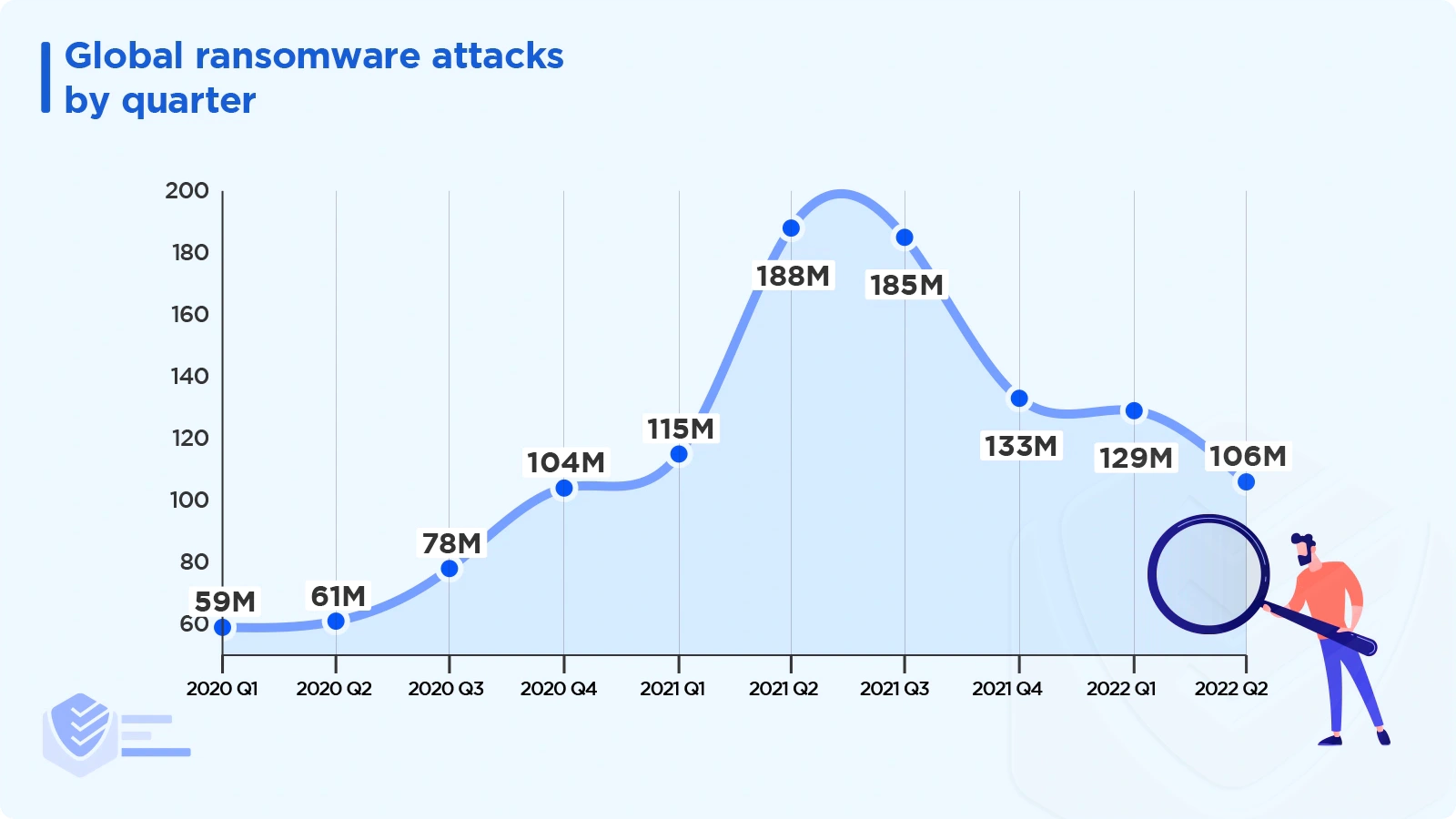
Between 2020 and Q2 2022, the volume of ransomware attacks peaked in Q2 2021 with 188.9 million attacks. [SonicWall]
Ransomware remains the most common form of malware in 2022. It has grown in popularity due to its capacity to extort large sums of money while posing a low risk to cybercriminals. [Cybereason]
Ransomware is the second leading cause of data breaches in Q1 2022, after phishing. [Identity Theft Resouce Center]
There were 623.3 million ransomware attacks worldwide in 2021 and 304.6 million detected attacks in 2020. [Statista]
In the first half of 2022, there were 236.1 million ransomware attempts. [Statista]
Although the majority of machines targeted are Windows and Mac based, there has been a 146% increase in Linux ransomware. [IBM Security]
76% of organizations suffered one or more ransomware attacks in 2021. Of those 76%:
42% were unintentionally caused by user actions, such as clicking on malicious links from spam emails.
43% were due to negligence from managers or administrators (risks concerning software patches, credentials, etc.) [Veeam]
In 2021, hackers successfully encrypted data in 65% of attacks, up from 54% recorded in 2020. [Sophos]
In 2021, there was an 82% rise in ransomware incidents, with 2,686 attacks as opposed to 1,474 in 2020. [CrowdStrike]
During the first half of 2022, there were 707 ransomware attempts per organization. [SonicWall]
Countries targeted by ransomware
Ransomware criminal groups mainly target richer countries to maximize profits.
Industries targeted by ransomware
Although all industry sectors can be targeted by ransomware, some industries are more vulnerable than others.
The sectors that ransomware affected the most in 2021 include Legal (92%), Manufacturing (78%), Financial Services (78%), and Human Resources (77%). [Cybereason]
Criminals used ransomware against 14 of the 16 critical infrastructure sectors (US), including Emergency Services, Food and Agriculture, IT, and Government Facilities. [Cybereason]
86% of private sector companies reported that ransomware cost them dearly in terms of revenue and/or business in 2021. [Sophos]
In 2021, the retail industry experienced the most significant increase in ransomware — 100%. Compared to 2020, the technology sector saw an 89% increase, and healthcare shot up by 30%. [BlackFog]
The impact of ransomware on businesses
Companies affected by ransomware suffer tremendous losses, such as losing millions of dollars, losing customers, and even losing employees.
The cost of ransomware
Here’s how much ransomware attacks cost businesses in 2021:
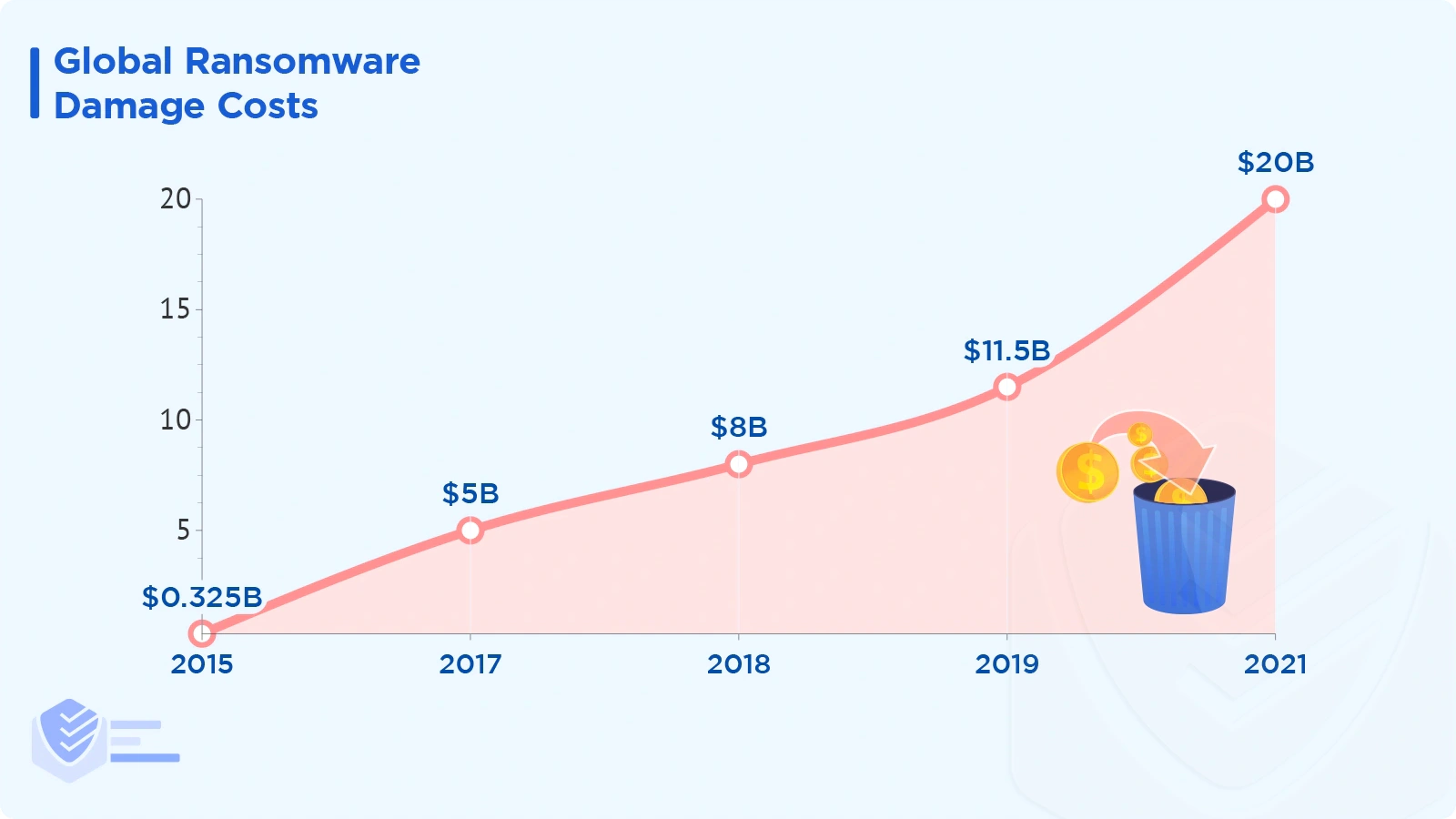
Between 2015 and 2021, the global cost of ransomware increased dramatically: from $325 million in 2015 to $20 billion in 2021.
67% of affected firms reported losses ranging from $1 million to $10 million from ransomware attacks. [Cybereason]
4% of affected companies estimated losses from $25 million to $50 million. [Cybereason]
Following a ransomware attack, 37% of respondents indicated their company had to fire staff, which is over 30% more than in 2021. [Cybereason]
35% of respondents experienced C-level resignations following a ransomware attack. [Cybereason]
33% of respondents were forced to temporarily stop operations in 2022, up 7% points from 2021. [Cybereason]
The number of organizations targeted by ransomware attacks grew by 33% in the first half of 2022 (73%) compared to 2021 (55%). [Cybereason]
In 2021, about 66% of organizations experienced losses due to ransomware, up from 37% in 2020. This is an increase of 78% in one year, which shows that adversaries are getting much better at launching large-scale attacks. [Sophos]
The average size of a target company was 15,581 employees in 2021, a decrease of 31% compared with 2020. [BlackFog]
90% of those hit by ransomware in 2021 said that their operations were severely disrupted. [Sophos]
The average cost to a business in 2021 to repair the impact of a ransomware assault was $1.4 million. This is a significant decrease from $1.85 million in 2020. [Sophos]
Of the organizations hit by ransomware in 2021, 66% were attacked 3 or more times. More than 10 distinct attacks impacted around 15% of organizations. [Proofpoint]
Ransom payments stats
Some companies choose to pay the ransom, even though it’s generally not recommended and even illegal in some countries.
The global average ransom payment was over $200,000 in the first half of 2022. That’s almost the same compared to 2021 — 204K — and considerably more than the average in 2020 — 169K. [Coveware]
The median payment was under US$100,000 in the first half of 2022. [Coveware]
Fewer organizations paid a ransom in Q1 2022 (less than 50%) compared to Q1 2019 (85%). [SonicWall]
In 2021, the number of victims paying $1 million for ransom tripled (11%) compared to 2020. [Sophos]
The proportion of organizations paying less than $10,000 dropped to 1 in 5 in 2021 from 1 in 3 in 2020. [Sophos]
The manufacturing and production sector experienced the highest average ransom payments in 2021 — $2.04 million. [Sophos]
The lowest average payments in 2021 were in healthcare — 197K. [Sophos]
Ransomware data recovery statistics
Businesses either paid or had different recovery methods to get their data back. Here are the facts.
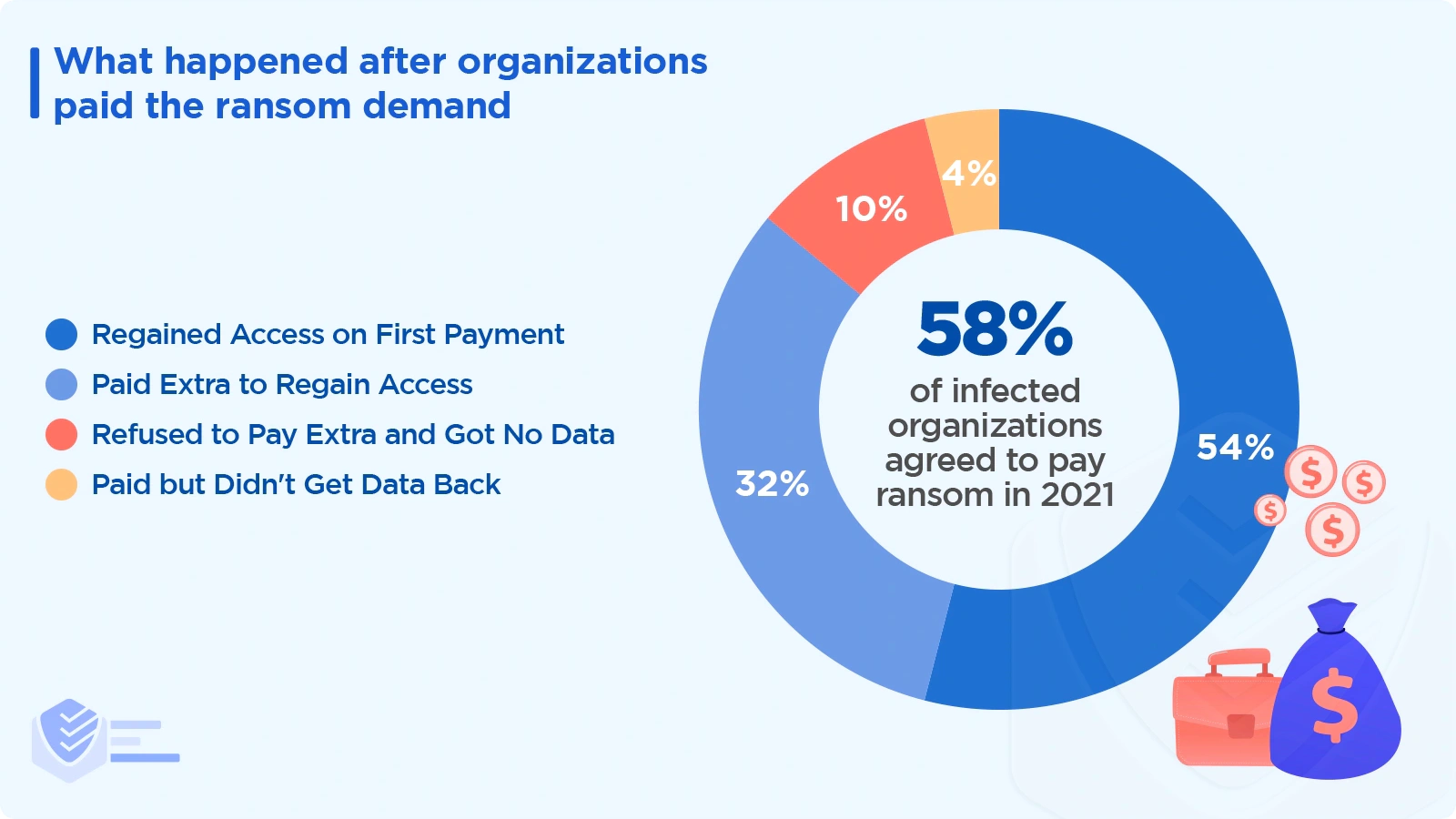
58% of victims paid their attackers in 2021. Of those that paid:
54% regained data after the first payment
32% regained access after paying additional ransom demands
10% refused to pay extra and didn’t recover any data
4% paid but did not regain access to their data or systems. [Proofpoint]
In 2021, 99% of all businesses affected by ransomware recovered at least some of their data, up slightly from 96% in 2020. [Sophos]
Just 4% of payers got their data back in its entirety, down from 8% in 2020. [Sophos]
44% of the respondents whose company's data had been encrypted used various techniques to restore it without paying. [Sophos]
Backups are the most popular approach for recovering data, with 73% of companies with encrypted data having backups. [Sophos]
80% of those who paid were hit by ransomware a second time. [Cybereason]
68% of payers were hit by ransomware less than a month later. The attackers demanded larger sums of money. [Cybereason]
44% of these organizations paid the second ransom. 9% were asked to pay 3 times more, which they did. [Cybereason]
88% of organizations targeted for repeated attacks have over 1,500 employees. [Cybereason]
42% of payers said the payment resulted in partial data recovery. [Cybereason]
78% of non-payers said they fully restored encrypted data without receiving a decryption key from attackers. [Cybereason]
Why do businesses pay ransoms?
Businesses pay ransoms for a variety of reasons, including:
49% of organizations said they paid to avoid revenue losses. [Cybereason]
41% said the desire to speed up recovery was the primary reason for payment. [Cybereason]
27% said they paid the ransom because they hadn’t made data backups. [Cybereason]
34% stated they didn't have enough employees to attempt recovery properly without the help of the attackers. [Cybereason]
28% said they paid the ransom to avoid delays in recovery that could result in injury or death. [Cybereason]
Data exfiltration, also known as unauthorized data removal or movement, is another concern for businesses. 77% of all ransomware attacks came with threats to publish exfiltrated data if a ransom was not paid. [Cybereason]
In 54% of data exfiltration cases, the exfiltrated data included sensitive customer data; 34% was Personal Identifiable Information (PII); 30% included Intellectual Property (IP); 27% was Protected Health Information (PHI). [Cybereason]
In 1 in 3 data breaches involving ransomware, data was exfiltrated to China or Russia. [BlackFog]
How well do businesses combat ransomware?
The threat of a ransomware attack causes businesses to increase their cyber security protection measures. Get more details below.
Companies are better at recovering data
Companies that invest more resources into combating ransomware are better equipped to recover lost data. Learn more:
In 2022, 88% of organizations reported that they believe they have the right talent to defend against ransomware attacks. That's nearly a 50% increase compared to 60% last year. [Cybereason]
94% of all surveyed organizations state they have an incident response plan in place. [ThycoticCentrify]
75% of respondents said their company has the proper contingency strategies in place to combat ransomware attacks. [Cybereason]
The influence of ransomware on security budgets
Ransomware is one of the most important reasons for business security spending.
86% of respondents have invested more money to better guard against ransomware attacks. [Cybereason]
66% of respondents said their security budget increased between 11% and 50%. [Cybereason]
93% of respondents have purchased cyber insurance, up from 75% in 2020. [Cybereason]
Most ransomware prevention resources are invested in Network Security (49%) and Cloud Security (41%) solutions. [ThycoticCentrify]
Ransomware encourages cyber insurance coverage
More and more businesses purchase cyber insurance to combat ransomware attacks.
It has been hard for most companies (94%) to get coverage in 2021 due to the high number of ransomware attacks.
54% say there are higher cybersecurity requirements for getting coverage
47% state that policies are now more complex than ever
40% say fewer companies offer cyber insurance
37% say the process takes longer
34% say it costs more money [Sophos]
84% of the insured stated that their cybersecurity policies include ransomware coverage, up from just 54% in 2020. [Cybereason]
83% of respondents said their organization has cyber insurance with ransomware protection. However, 34% state there are exclusions or exceptions in their policy. [Sophos]
The sectors that are most likely to have coverage are energy, oil/gas, and utilities (89%). [Sophos]
88% of 3,000-5,000 employee organizations purchased cybersecurity insurance. In contrast, only 73% of those with 100-250 employees have coverage. [Sophos]
Among those who were not targeted but did not anticipate an attack, cyber insurance coverage was 61%. [Sophos]
Those who said their insurance covered the costs to return to normal rose from 67% in 2019 to 77% in 2021. [Sophos]
Does cyber insurance cover ransomware losses?
Organizations investing in cyber insurance hope that insurers will cover ransomware losses. But is that actually happening?
Cyber insurance policyholders were 98% more likely to receive compensation in the most significant ransomware attacks in 2021. However, not all of these are ransomware payments per se. In 77% of cases, the insurer paid the costs to help the organization resume its operations (cleanup costs), and only 40% reported that the insurer paid the ransom. [Sophos]
The sector with the highest payment rate is secondary education, with 53%. The lowest rates were reported in manufacturing and production, with 30%. [Sophos]
Ransomware recovery stats
How fast did companies get back on their feet after a ransomware attack?
In 2021, companies took 1 month on average to recover from a major ransomware attack. [Sophos]
The longest time to recuperate was in the education and central/federal government sectors, where 40% of organizations required more than 1 month to recover. Sophos]
The fastest recovery was seen in the manufacturing and production sectors, where 10% of respondents took 1 month to recover. [Sophos]
Ransomware families and attack vectors
Ransomware attacks are perpetrated by global criminal organizations that employ different methods of attack.
The top 5 ransomware families
These were the most common ransomware families/organizations in 2021:
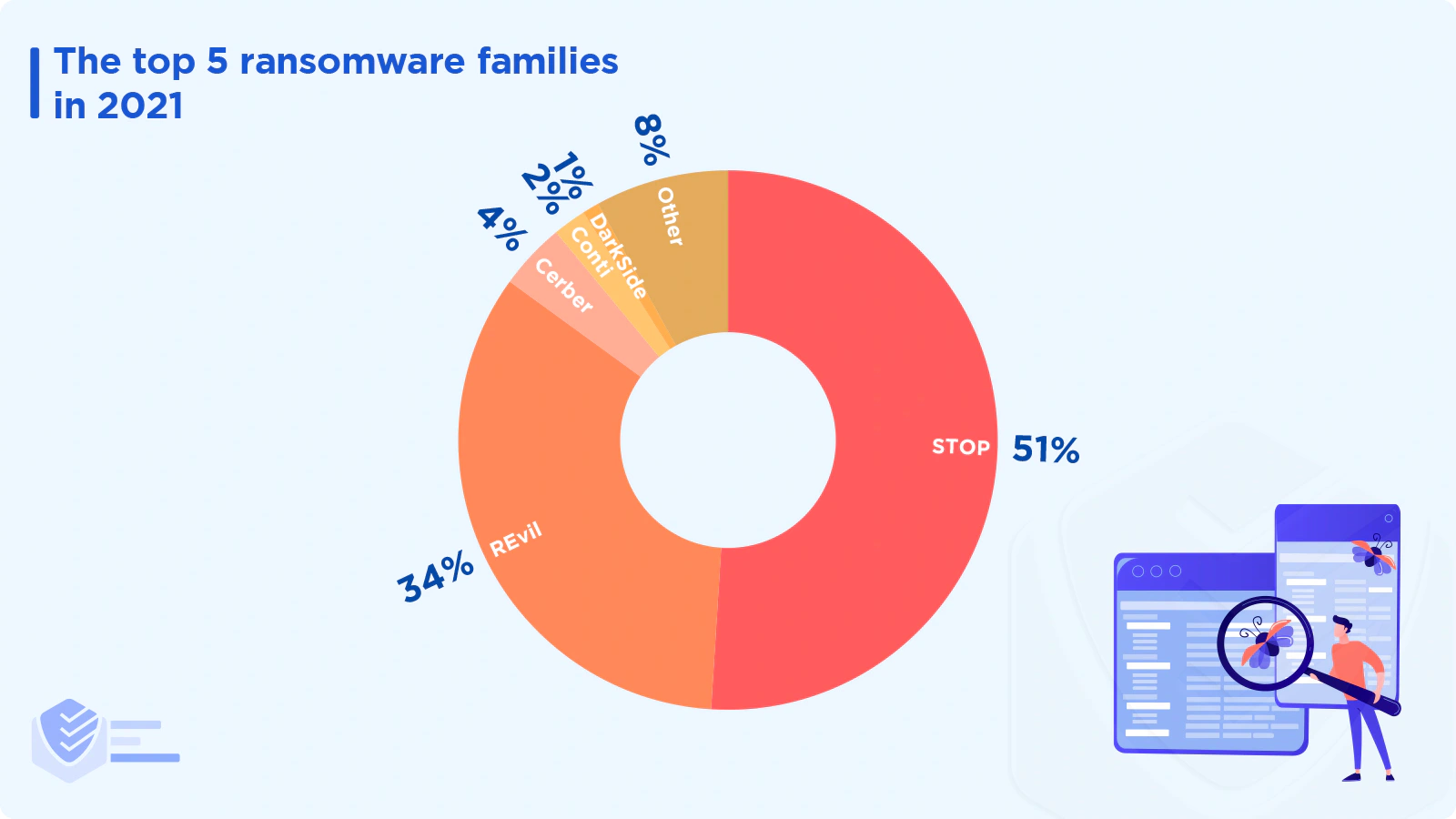
STOP (51%) — This ransomware family encrypts files on a victim’s machine using encryption algorithms such as AES-256. STOP targets the most widely used file types, including photos, videos, music, PDFs, Microsoft Office documents, databases, archives, and apps. [Deep Instinct]
REvil (34%) — Also known as Sodinokibi, Revil infected more than 1,500 companies in early 2021. The most destructive attack was on American software vendor Kaseya VSA. REvil’s attack affected over 1 million users. The $70 million ransom demand is the largest ever recorded. Hundreds of supermarkets had to close for several days. [Deep Instinct]
Cerber (4%) — Cerber was the most prevalent ransomware program until recently, accounting for more than 25% of all infections in mid-2017. Cerber targets users from all around the world, although it avoids former Soviet-block nations. [Deep Instinct]
Conti (2%) — This ransomware strain has grown dramatically and is now one of the most common malware variants. Conti typically targets organizations based in the US and Eastern Europe. [Deep Instinct]
DarkSide (1%) — This type of ransomware functions as a RaaS (Ransomware-as-a-Service) and targets organizations in English-speaking countries. Affiliates must also avoid targeting sectors like healthcare and education. [Deep Instinct]
Other statistics about ransomware families
In 2021, there were no attacks from ransomware groups like Ryuk and Nefilim Maze. DoppelPaymer's attacks were also reduced by 160%. [Deep Instinct]
In the first half of 2022, the top 3 ransomware families include Cerber (43 million hits), Ryouk (34 million hits), and GrandCrab (16 million hits). [SonicWall]
Ransomware gangs have an average lifespan of 17 months before disappearing or rebranding to another criminal group. [IBM Security]
Ransomware attack vector statistics
Check out some of the top statistics about ransomware attack vectors, i.e. tools and tactics to infiltrate systems and networks:
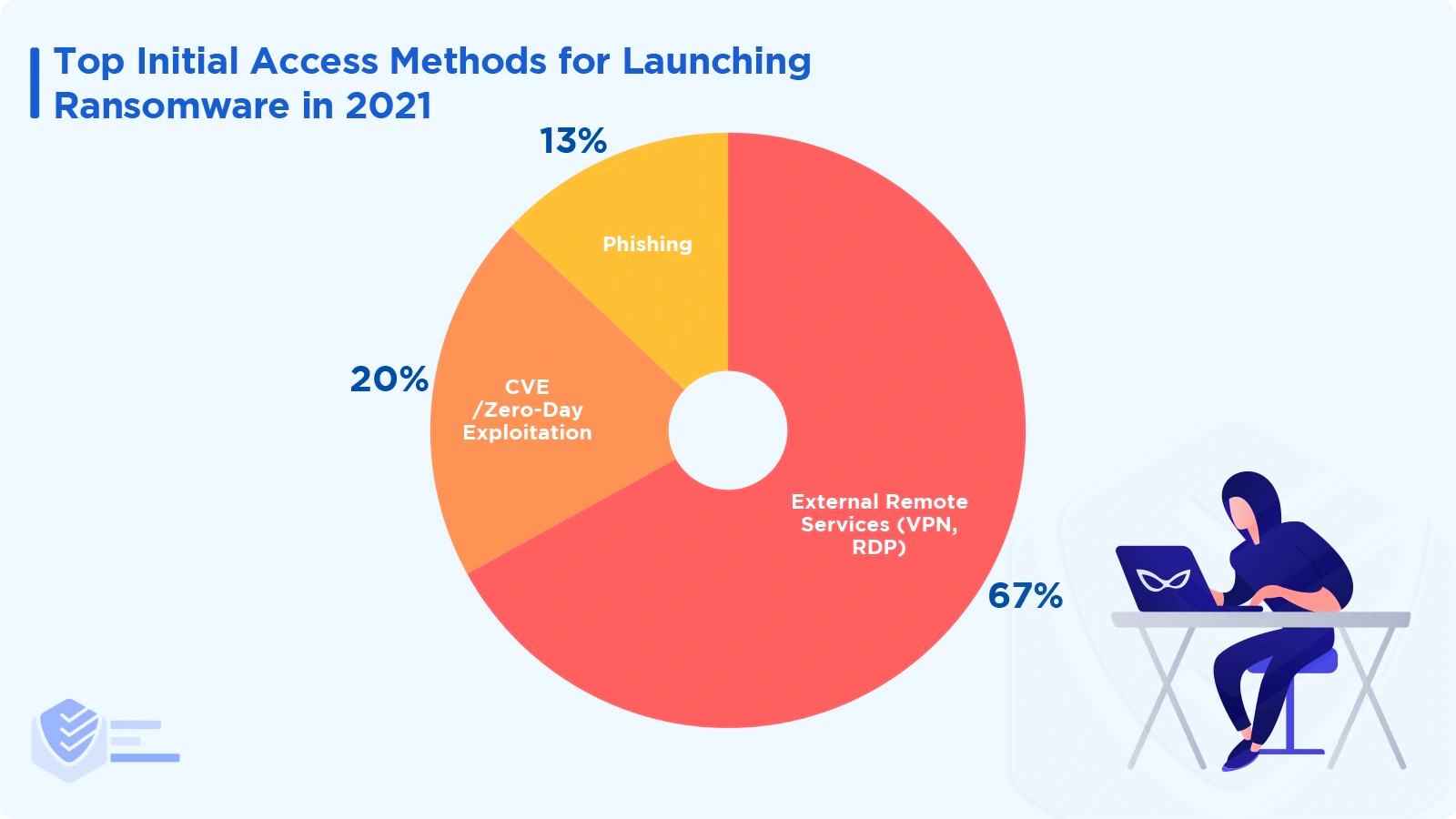
The most common methods for infecting systems with ransomware include external remote services (67%), zero-day exploits (20%), and phishing (13%).
1 out of 3 hackers used botnets and 2 out of 3 used illegal networks. [BlackFog]
80% of ransomware infections are accomplished via PowerShell. [BlackFog]
Desktop-sharing software was used in 40% of ransomware incidents. Also, email was involved in 35% of the incidents. [Verizon]
Of the organizations that suffered a ransomware attack in the past 2 years, 63% said that the attackers breached their networks 6 months prior to being detected; 21% for 7 to 12 months; and 16% for 12 months or more. [Cybereason]
64% of organizations were attacked by ransomware due to a third-party supply chain compromise. [Cybereason]
The organizations most vulnerable to supply chain attacks were small to medium-sized. [Cybereason]
To steal legitimate credentials, more than 80% of cyber assaults rely on identity-based attacks. [CrowdStrike]
Ransomware predictions for 2023 and beyond
Here’s what top publications have to say about the future of ransomware.
It is estimated that the cost of ransomware will be over $42 billion by the end of 2024 and over $265 billion by 2031. [Cybersecurity Ventures]
By 2025, the number of ransomware attacks will increase by 700%. [Gartner]
At least 75% of organizations will be targeted more than once by 2025. [Gartner]
By the end of 2025, 30% of countries will pass legislations to regulate payments, fines, and negotiations regarding ransomware. Less than 1% of states do so as of 2021. [Gartner]
Sources
Annual number of ransomware attacks worldwide from 2016 to first half 2022 — Statista
2021 Ransomware Attack Report — BlackFog
First Quarter 2022 Data Breach Analysis — Identity Theft Resource Center
The State of Ransomware 2022 — Sophos
Ransomware: The True Cost to Business 2022 — Cybereason
2022 Global Threat Report — CrowdStrike
2022 Threat Review — Malwarebytes
2022 State of the Phish — Proofpoint
Ransomware Trends in the HPH Sector (Q1 2022) — HHS Cybersecurity Program
Advanced Threat Research Report: January 2022 — Trellix
Data Breach Investigations Report — Verizon
Mid-Year Update: 2022 Cyber Threat Report — SonicWall
X-Force Threat Intelligence Index 2022 — IBM Security
The Top 8 Cybersecurity Predictions for 2021-2022 — Gartner
State of Ransomware Survey & Report 2021 — ThycoticCentrify
2022 Cyberthreat Defense Report — Cyberedge
2022 Data Protection Trends Report — Veeam
Fewer Ransomware Victims Pay, as Median Ransom Falls in Q2 2022 — Coveware
The Ransomware Threat Landscape: What to Expect in 2022 — Symantec
Q2 2022 Threat Landscape: Ransomware Returns, Healthcare Hit — Kroll
Octav Fedor (Cybersecurity Editor)
Octav is a cybersecurity researcher and writer at AntivirusGuide. When he’s not publishing his honest opinions about security software online, he likes to learn about programming, watch astronomy documentaries, and participate in general knowledge competitions.