The Mozilla Foundation teases and annoys the Firefox user this week. It teases the user by making a mockup of Firefox 4.0 available to the public – this after a theme mockup of the upcoming Firefox 3.7 was announced a short while ago (here’s how you can get your Firefox browser to look like that theme mockup). Then it annoys the user by announcing a new security hole in the browser it developed: a URL bar spoofing vulnerability that affects all versions of Firefox.
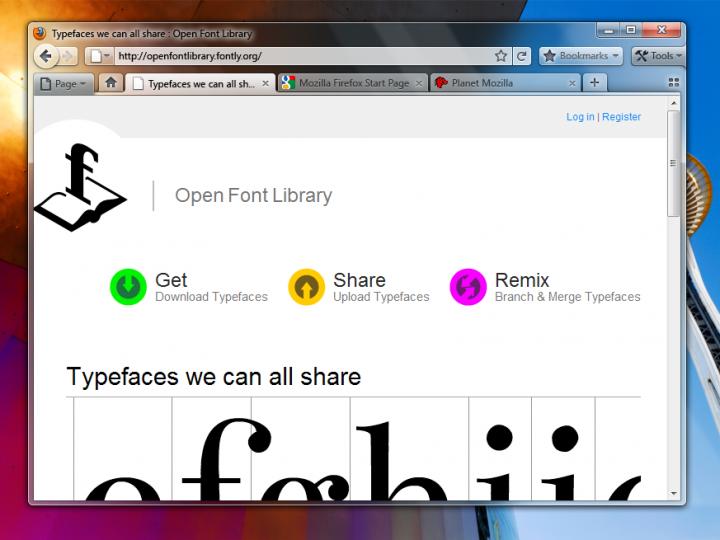
Starting with the Firefox 4.0 mock-up, two versions have been proposed: one with tabs on bottom (version A – image below) and one with tabs on top (version B – image below as well). The later option comes with some upsides: it saves vertical space, it is more efficient as it removes visual complexity, and there’s a shorter mouse distance to Page Controls. On the downside it breaks consistency (existing users are familiar with the current design and like this familiarity with the browser), tab titles are missing, there’s a longer mouse distance to tabs, some space is needlessly lost.
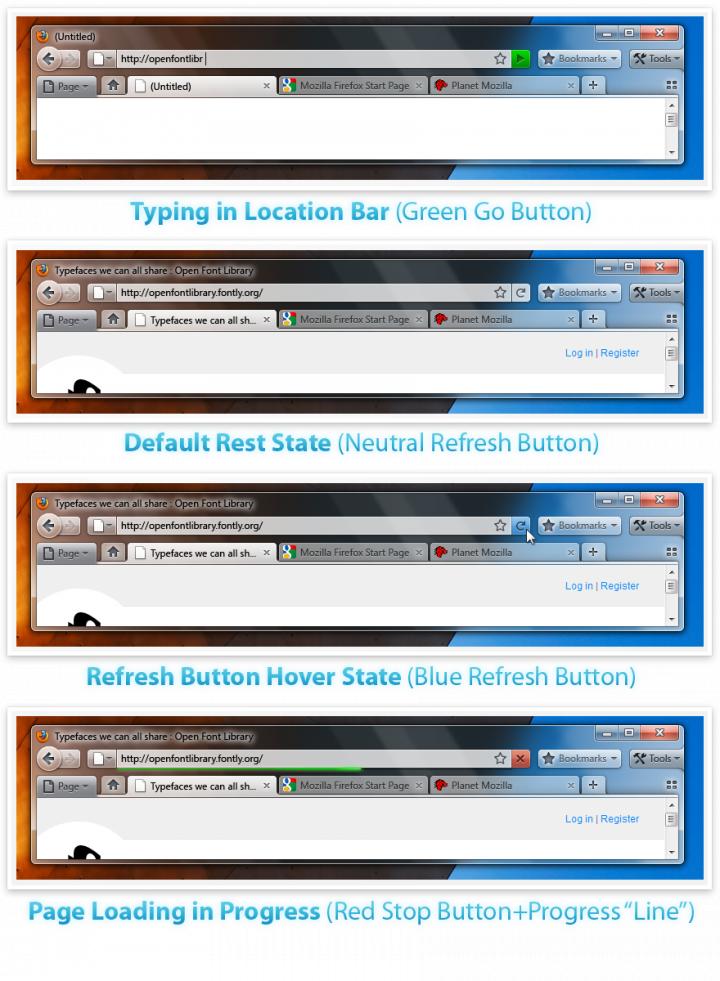
It has also been proposed to blend together the Stop, Refresh and Go buttons. This Stop/Refresh/Go Button would turn green when you start typing, will blend with the location bar when not in use, will turn blue when you hover over it, and will turn red when a page loads. Check out the images below.
Moving on, the Mozilla Security team announced that a URL spoofing security vulnerability affecting all current versions of the Firefox browser has been discovered – the credit for discovering this security hole goes to Juan Pablo Lopez Yacubian. The only workaround that you can employ is to share confidential info only with websites that you opened from a bookmark, a trusted source, or sites that you accessed by typing in the URL yourself.
Official word from Mozilla: “The URL in the address bar can be spoofed when a new window or tab is opened by a malicious web page. If a user visits a page hosting this malicious code, a new window or tab can be opened with a faked URL. There is no way of determining if the URL is authentic. This could result in the user disclosing confidential information to the malicious site, known as a phishing attack. This vulnerability is known to affect all current versions of Firefox. Mozilla is actively working on fixing this vulnerability.”
Version A
Version B
Stop/Refresh/Go Button
Starting with the Firefox 4.0 mock-up, two versions have been proposed: one with tabs on bottom (version A – image below) and one with tabs on top (version B – image below as well). The later option comes with some upsides: it saves vertical space, it is more efficient as it removes visual complexity, and there’s a shorter mouse distance to Page Controls. On the downside it breaks consistency (existing users are familiar with the current design and like this familiarity with the browser), tab titles are missing, there’s a longer mouse distance to tabs, some space is needlessly lost.
It has also been proposed to blend together the Stop, Refresh and Go buttons. This Stop/Refresh/Go Button would turn green when you start typing, will blend with the location bar when not in use, will turn blue when you hover over it, and will turn red when a page loads. Check out the images below.
Moving on, the Mozilla Security team announced that a URL spoofing security vulnerability affecting all current versions of the Firefox browser has been discovered – the credit for discovering this security hole goes to Juan Pablo Lopez Yacubian. The only workaround that you can employ is to share confidential info only with websites that you opened from a bookmark, a trusted source, or sites that you accessed by typing in the URL yourself.
Official word from Mozilla: “The URL in the address bar can be spoofed when a new window or tab is opened by a malicious web page. If a user visits a page hosting this malicious code, a new window or tab can be opened with a faked URL. There is no way of determining if the URL is authentic. This could result in the user disclosing confidential information to the malicious site, known as a phishing attack. This vulnerability is known to affect all current versions of Firefox. Mozilla is actively working on fixing this vulnerability.”
Version A

Version B

Stop/Refresh/Go Button


























