April Fools has come and gone, the Conficker worm has been updated, but nothing spectacular happened. Why spectacular? Because the media hyped the 1st of April Conficker update so much that we were expecting for some sort of pandemonium, which failed to appear. Think of it as the Y2K scare that saw just as much media exposure, if not more, but which in the end proved to be just that – a scare.
Director of Technical Education with Eset, company better known for their Nod 32 and Eset Smart Security app, Randy Abrams comments: “I kept telling everyone to worry about being secure, not about Conficker. Some people listen, some don’t. According to ESET’s ThreatSense.Net, by about 2 PM GMT on April 1st, of the top 20 threats encountered by our users in the past 24 hours, four out of five of them were NOT Conficker. About 16.17% of the threats were online game password stealing threats. Another 21.5% were threats that were not Conficker and were trying to use Autorun to infect computers. 9.72% of the threats were something we call Win32/Agent, which tries to steal data from your computer. Yes, 80% of the risk was not Conficker but 99% of the attention was on Conficker. Does that make sense to you? Can you imagine crossing the street and ignoring 4 out of 5 cars? Do you think you’ll live long?”
So what did happen? According to MSRC (Microsoft Security Response Team) the Conficker worm started using the new domain generation algorithm that security experts were expecting the worm to use. No new variants of the Conficker worm have been released; no new methods of attacks have been detected as well.
Now that the Conficker scare has come and passed, a new controversy has spurred: who started it all? The media says it was the security experts who blew the whistle on this one, but blew it a bit too hard, leading users to be needlessly scared of a phenomenon that never materialized. Security experts on the other hand say they always advised people to be cautious of security in general, and advised users to be cautious about the Conficker worm without getting too worked up about it all.
Senior Technology Consultant with Sophos, Graham Cluley: “I actually think most of the computer security industry were remarkably reserved and sane during the build up to Conficker, reminding people that there was no guarantee that the worm would do anything noticeable at all and that it was quite prossible (prosibble is a combination of the words "probable" and "possible") that hackers wouldn't give Conficker-infected PCs any new instructions. In fact, in my own experience, it has been some of the newspapers and media organizations who have been guilty of dreaming up apocalyptic headlines and the security vendors who have been pouring the cold water.”
Graham Cluley’s post comes in answer of an article written by Charles Arthur, entitled “Antivirus companies’ worst fears realized as Conficker does…nothing” and published on the online version of The Guardian (read article here).
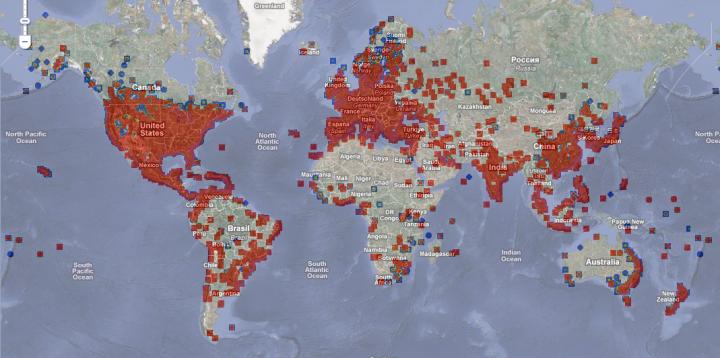
If you would like to see just how widespread the Conficker worm is, a map has been made available by F-Secure.
Director of Technical Education with Eset, company better known for their Nod 32 and Eset Smart Security app, Randy Abrams comments: “I kept telling everyone to worry about being secure, not about Conficker. Some people listen, some don’t. According to ESET’s ThreatSense.Net, by about 2 PM GMT on April 1st, of the top 20 threats encountered by our users in the past 24 hours, four out of five of them were NOT Conficker. About 16.17% of the threats were online game password stealing threats. Another 21.5% were threats that were not Conficker and were trying to use Autorun to infect computers. 9.72% of the threats were something we call Win32/Agent, which tries to steal data from your computer. Yes, 80% of the risk was not Conficker but 99% of the attention was on Conficker. Does that make sense to you? Can you imagine crossing the street and ignoring 4 out of 5 cars? Do you think you’ll live long?”
So what did happen? According to MSRC (Microsoft Security Response Team) the Conficker worm started using the new domain generation algorithm that security experts were expecting the worm to use. No new variants of the Conficker worm have been released; no new methods of attacks have been detected as well.
Now that the Conficker scare has come and passed, a new controversy has spurred: who started it all? The media says it was the security experts who blew the whistle on this one, but blew it a bit too hard, leading users to be needlessly scared of a phenomenon that never materialized. Security experts on the other hand say they always advised people to be cautious of security in general, and advised users to be cautious about the Conficker worm without getting too worked up about it all.
Senior Technology Consultant with Sophos, Graham Cluley: “I actually think most of the computer security industry were remarkably reserved and sane during the build up to Conficker, reminding people that there was no guarantee that the worm would do anything noticeable at all and that it was quite prossible (prosibble is a combination of the words "probable" and "possible") that hackers wouldn't give Conficker-infected PCs any new instructions. In fact, in my own experience, it has been some of the newspapers and media organizations who have been guilty of dreaming up apocalyptic headlines and the security vendors who have been pouring the cold water.”
Graham Cluley’s post comes in answer of an article written by Charles Arthur, entitled “Antivirus companies’ worst fears realized as Conficker does…nothing” and published on the online version of The Guardian (read article here).
If you would like to see just how widespread the Conficker worm is, a map has been made available by F-Secure.


























